Information Security Risk Management Framework
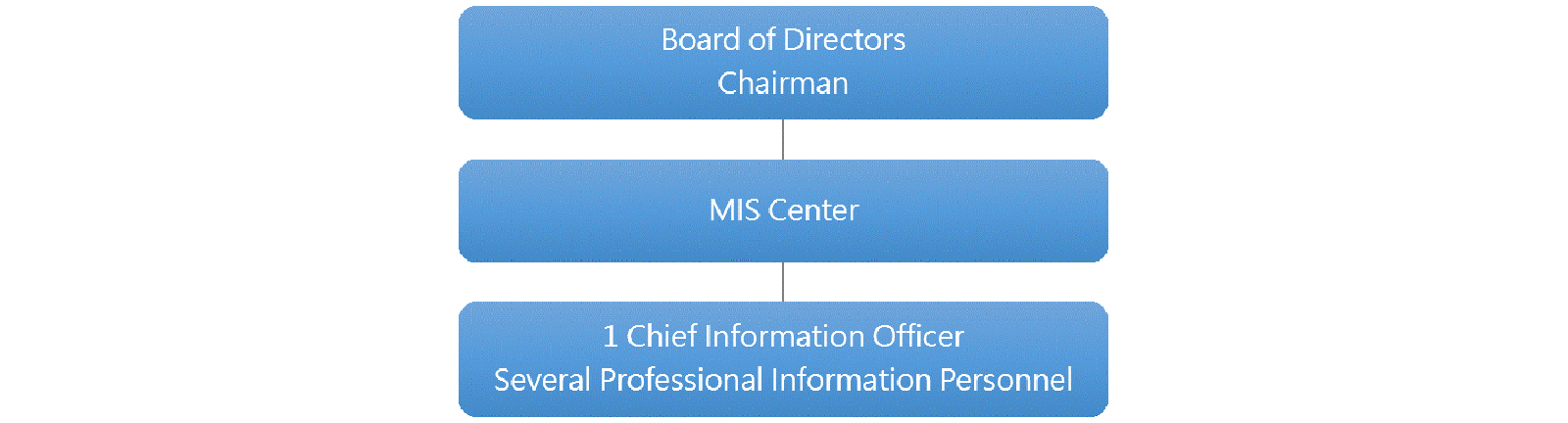
The company's information security authority is convened by the CEO and organizes the Information Management Center, which has a chief information officer and several professional information personnel responsible for coordinating and implementing information security policies, disseminating information security information, raising employees' awareness of information security, and collecting and improving technologies, products or procedures for the performance and effectiveness of the organization's information security management system.
The audit office conducts annual information security audits on the internal control system (information system management information security inspection operations) to evaluate the effectiveness of the company's internal controls over information operations.
The information security policy and its implementation are reviewed and reported to the Board of Directors on an annual basis.
